Vulnerability Scanning
Internal Network Vulnerability Scanning
Internal network security is critical yet often overlooked. Once attackers gain initial access through configuration drift, phishing, or compromised credentials, they can rapidly expand their foothold by exploiting internal vulnerabilities. This lateral movement can lead to devastating breaches, making internal vulnerability scanning as crucial as external assessments.
ProjectDiscovery offers two distinct approaches for internal network vulnerability scanning, each designed to fit different organizational needs while maintaining our core focus on exploitability and accurate detection.
Cloud-Managed Scanning
Use TunnelX for remote scan triggering through PDCP UI. Perfect for large networks and centralized security management.
Local Scanning & Upload
Run Nuclei locally and upload results to PDCP. Ideal for teams with existing scanning workflows or specific network restrictions.
Internal scanning helps identify misconfigurations, unpatched systems, and security gaps that could be exploited for lateral movement before attackers can leverage them.
Port Discovery with Naabu
Before running vulnerability scans, it’s recommended to first identify open ports in your internal network using Naabu - a fast and reliable port scanner. This ensures comprehensive vulnerability scanning coverage.The discovered ports can be used as input for vulnerability scanning to ensure thorough coverage of all exposed services. Learn more about Naabu’s capabilities in our detailed documentation.
Naabu will soon be integrated directly into ProjectDiscovery’s internal vulnerability scanning capabilities. Contact our sales team to be notified when this feature becomes available.
Method 1: Cloud-Managed Scanning (Recommended)
TunnelX is our open-source tunneling solution, purpose-built by ProjectDiscovery to enable secure internal scanning. It establishes isolated SOCKS5 proxies that let you trigger scans directly from the ProjectDiscovery interface while ensuring your internal infrastructure remains protected and unexposed.Cloud-managed internal scanning with TunnelX is an Enterprise-exclusive feature. Free users can still perform internal scans using the local scanning method described above.
System Requirements
TunnelX is designed to be lightweight and efficient. Minimum recommended specifications for optimal performance:
TunnelX is designed to be lightweight and efficient. Minimum recommended specifications for optimal performance:
- CPU: 1 vCPU/Core
- Memory: 2GB RAM
- Network: 100Mbps network interface
- Storage: 10GB available disk space
- Operating System: Linux (recommended), macOS, or Windows
Install TunnelX
Choose your preferred installation method:Triggering Internal Scans
Once you’ve successfully configured TunnelX, you can easily trigger internal scans directly from the ProjectDiscovery Cloud Platform:- Navigate to Scans Dashboard:
- Go to https://cloud.projectdiscovery.io/scans
- Click the “Create new scan” button
- Configure Your Scan:
- Set your targets, templates, and other scan configurations
- Proceed to the final “Scan settings” step
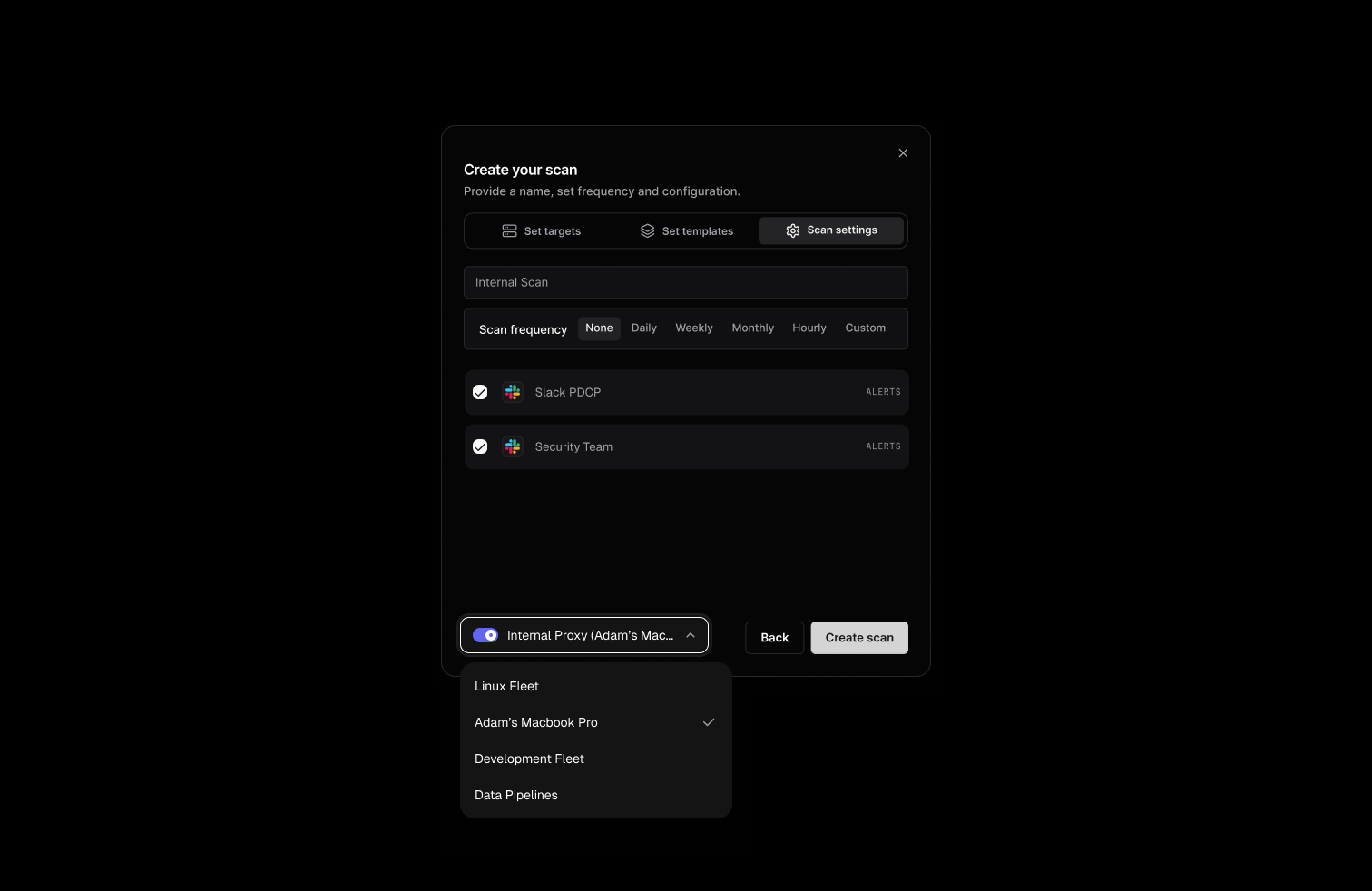
- Enable Internal Scanning:
- In the bottom left corner of the Scan settings screen, you’ll see an “Internal Scan” option
- Select this option to use your connected TunnelX proxy
- Choose the appropriate internal proxy connection from the dropdown

- Launch Your Scan:
- Click “Create scan” to start scanning your internal targets
TunnelX connections appear automatically in the dropdown once properly configured. If you don’t see your connection, check that TunnelX is running properly and your API key is correctly configured.
Important: Only input targets that are actually accessible from the machine where TunnelX is running. For example, if TunnelX is deployed on a server in your internal network (192.168.1.0/24), it can only scan hosts within that network or other networks it has routing access to. If you input external targets or internal hosts that the TunnelX machine cannot reach, the scan will fail.
Method 2: Local Scanning & Upload
This approach lets you run Nuclei locally and upload results to ProjectDiscovery Cloud Platform (ProjectDiscovery).Set up your API Key
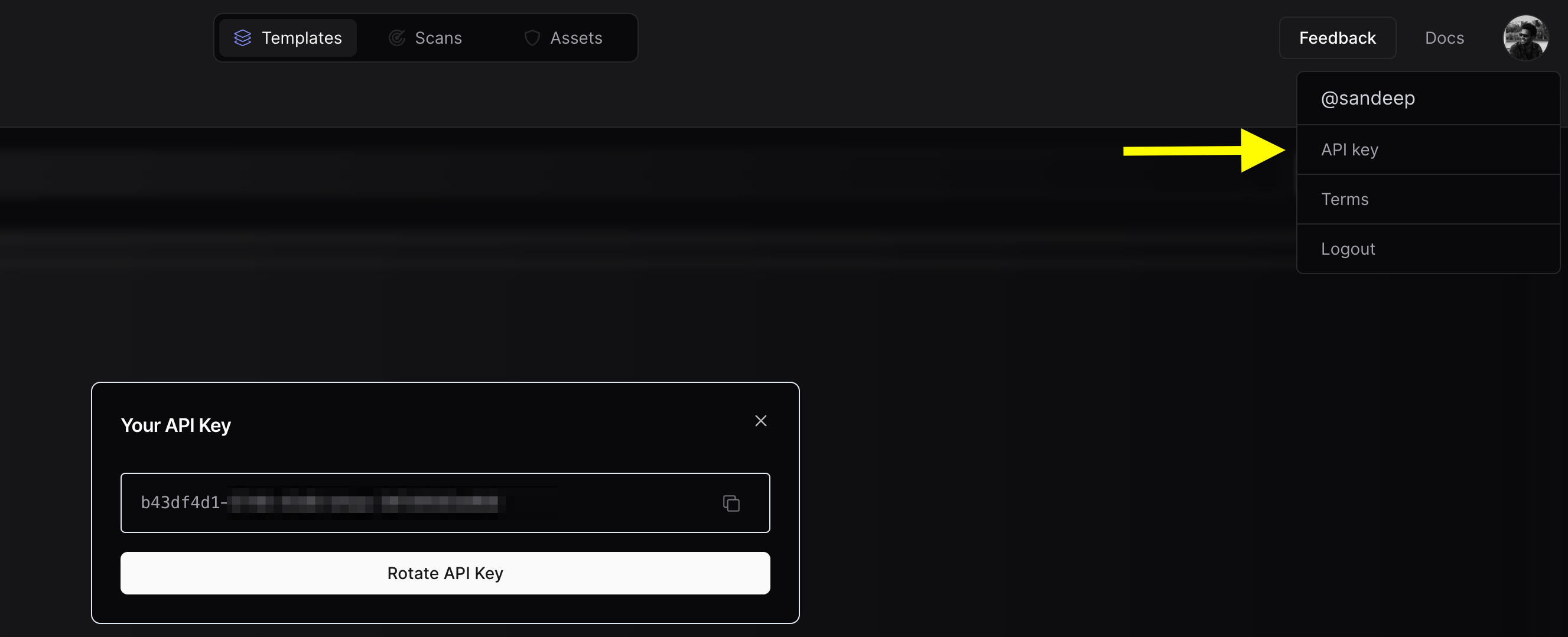
To connect your existing Nuclei results to PDCP you will need to create a free API Key:- Visit https://cloud.projectdiscovery.io
- Open the setting menu from the top right and select “API Key” to create your API Key

- Use the
nuclei -authcommand, and enter your API key when prompted.
Configure Team (Optional)
If you want to upload the scan results to a team workspace instead of your personal workspace, you can configure the Team ID using either method:-
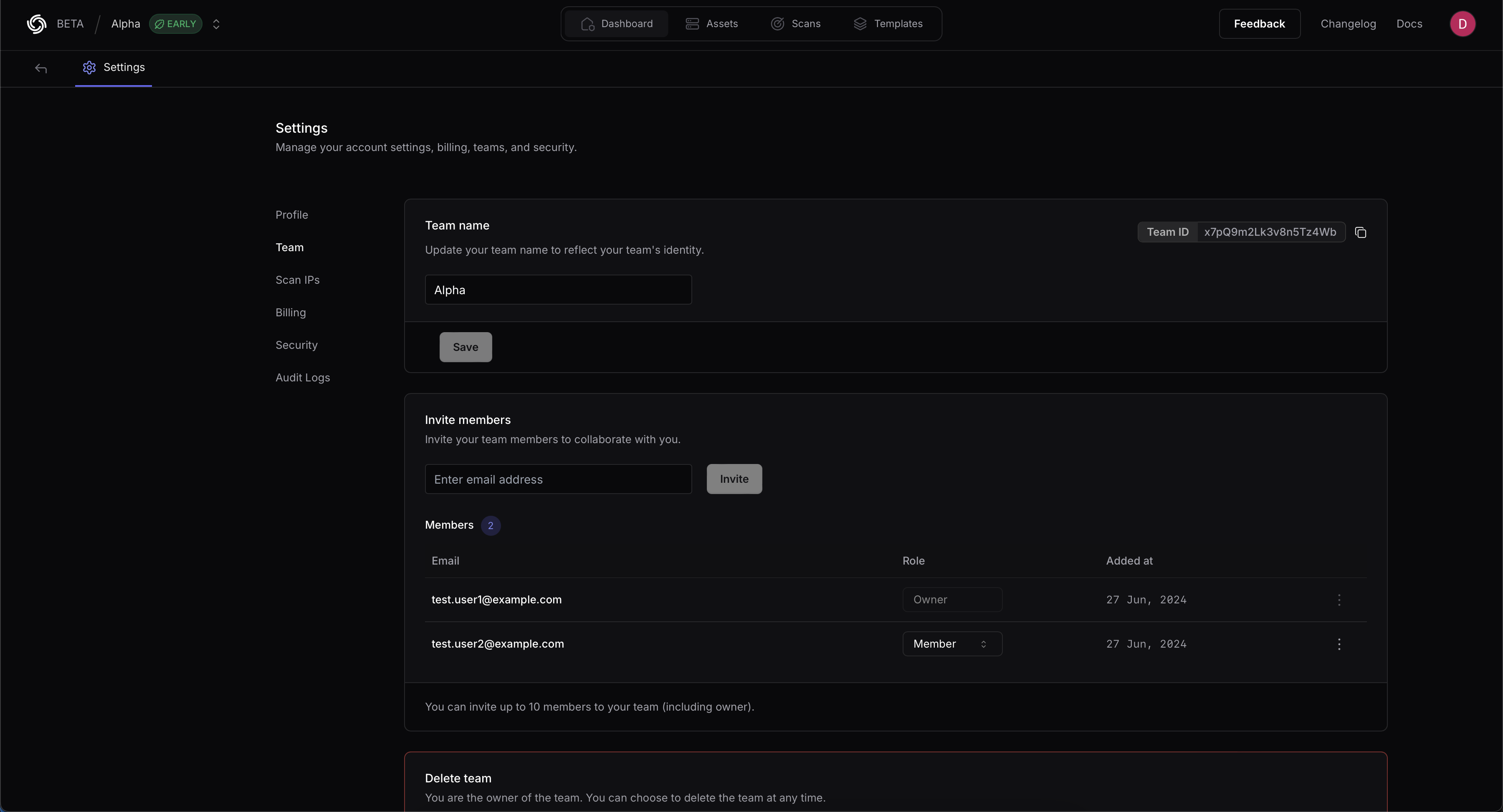
Obtain Team ID:
- Navigate to https://cloud.projectdiscovery.io/settings/team
- Copy the Team ID from the top right section
-
CLI Option:
-
ENV Variable:
- Run your scan with the upload flag:
This method is ideal when you want to maintain complete control over scan execution or integrate with existing automation scripts.

